Introduction:
What is Route53?
Amazon Route 53 (Route 53) is a scalable and highly available Domain Name System (DNS) service.
It is part of Amazon.com's cloud computing platform, Amazon Web Services (AWS).
The name is a reference to TCP or UDP port 53, where DNS server requests are addressed.In addition to being able to route users to various AWS services, including EC2 instances, Route 53 also enables AWS customers to route users to non-AWS infrastructure and to monitor the health of their application and its endpoints.
Route 53's servers are distributed throughout the world. Amazon Route 53 supports full, end-to-end DNS resolution over IPv6. Recursive DNS resolvers on IPv6 networks can use either IPv4 or IPv6 transport to send DNS queries to Amazon Route 53.
Customers create "hosted zones" that act as a container for four name servers.
The name servers are spread across four different TLDs. Customers are able to add, delete, and change any DNS records in their hosted zones.
One of the key features of Route 53 is programmatic access to the service that allows customers to modify DNS records via web service calls.
Combined with other features in AWS, this allows a developer to programmatically bring up a machine and point to components that have been created via other service calls such as those to create new S3 buckets or EC2 instances.
This will be really helpful where we are having split VPCs for different environments and need a single place for managing the DNS resolution from a single place.
It is part of Amazon.com's cloud computing platform, Amazon Web Services (AWS).
The name is a reference to TCP or UDP port 53, where DNS server requests are addressed.In addition to being able to route users to various AWS services, including EC2 instances, Route 53 also enables AWS customers to route users to non-AWS infrastructure and to monitor the health of their application and its endpoints.
Route 53's servers are distributed throughout the world. Amazon Route 53 supports full, end-to-end DNS resolution over IPv6. Recursive DNS resolvers on IPv6 networks can use either IPv4 or IPv6 transport to send DNS queries to Amazon Route 53.
Customers create "hosted zones" that act as a container for four name servers.
The name servers are spread across four different TLDs. Customers are able to add, delete, and change any DNS records in their hosted zones.
One of the key features of Route 53 is programmatic access to the service that allows customers to modify DNS records via web service calls.
Combined with other features in AWS, this allows a developer to programmatically bring up a machine and point to components that have been created via other service calls such as those to create new S3 buckets or EC2 instances.
What is the need for Peering of Route53 Hosted Zones?
This will be really helpful where we are having split VPCs for different environments and need a single place for managing the DNS resolution from a single place.
In a multi-account environment where you require connectivity between accounts, and perhaps connectivity between cloud and on-premises workloads, the demand for a robust Domain Name Service (DNS) that’s capable of name resolution across all connected environments will be high.
Reference Architecture:
Pre-Requisites and Assumptions:
- awscli installed and configured with appropriate credentials and region.
- VPC Peering done between the VPC's.
- ~Domain Names for PROD and NON-PROD VPCs are configured on R53.
- Account Mapping as below.
- Account-A --> PROD
- Account-B --> STAGE
STEPS:
- List Hosted Zones and their IDs from Account-A
- command: aws route53 list-hosted-zones
- command: aws route53 list-hosted-zones
In the above example output we can see the highlighted "Hosted Zone Name" and "Hosted Zone ID"
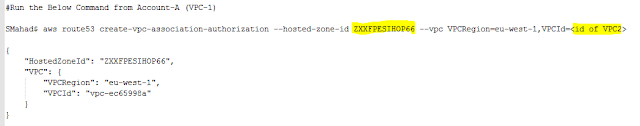
- Authorize the association between the private hosted zone in Account A and the VPC in Account B.
- command: aws route53 create-vpc-association-authorization --hosted-zone-id <hosted-zone-id> --vpc VPCRegion=<region>,VPCId=<vpc-id of Account-B>
Reference Output:
 |
| Authorize Association |
- Create the association between the private hosted zone in Account A and the VPC in Account B.
- command: aws route53 associate-vpc-with-hosted-zone --hosted-zone-id <hosted-zone-id> --vpc VPCRegion=<region>,VPCId=<vpc-id>
Reference Output:
- Delete the association authorization after the association is created.
Doing this prevents you from recreating the same association later.
To delete the authorization, reconnect to an EC2 instance in Account A
To delete the authorization, reconnect to an EC2 instance in Account A
- command: aws route53 delete-vpc-association-authorization --hosted-zone-id <hosted-zone-id> --vpc VPCRegion=<region>,VPCId=<vpc-id>



No comments:
Post a Comment